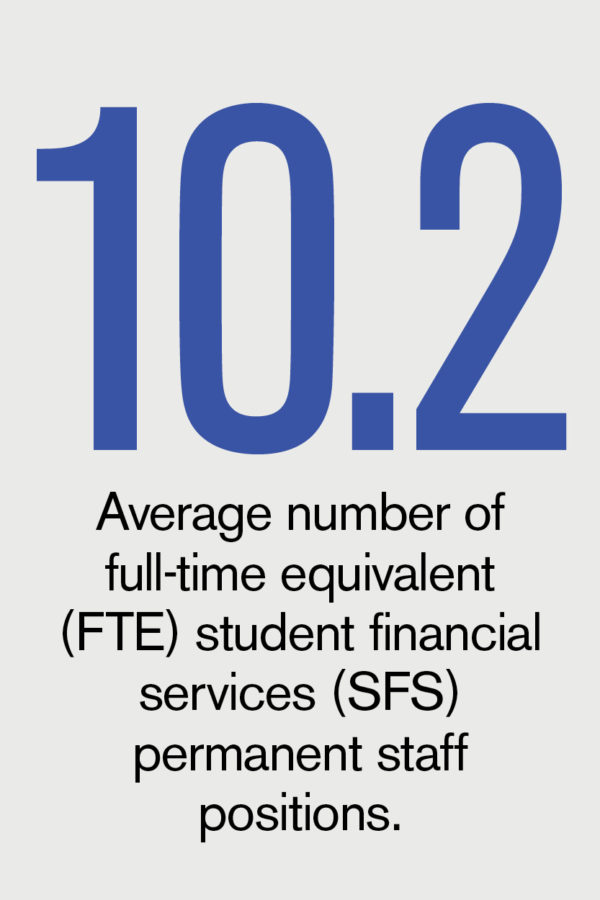
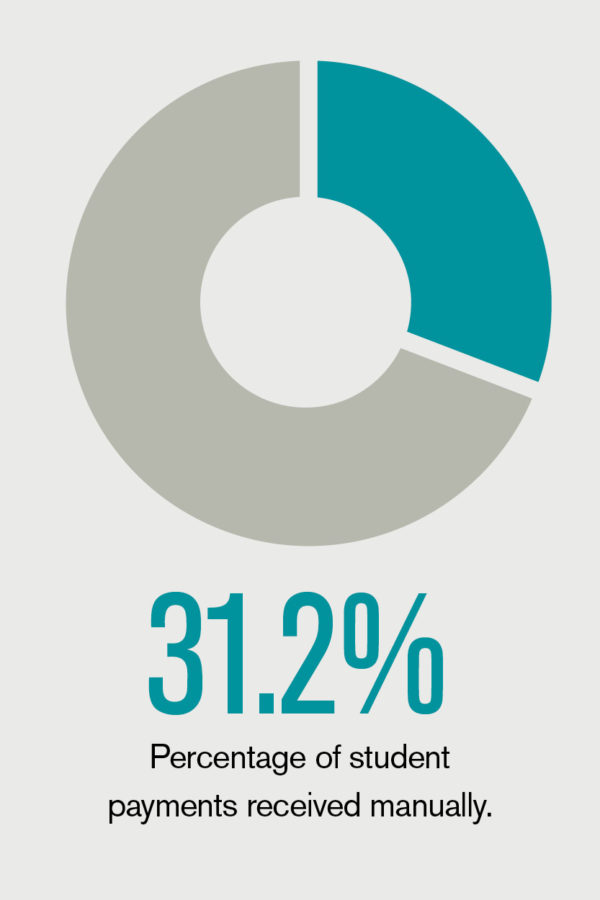
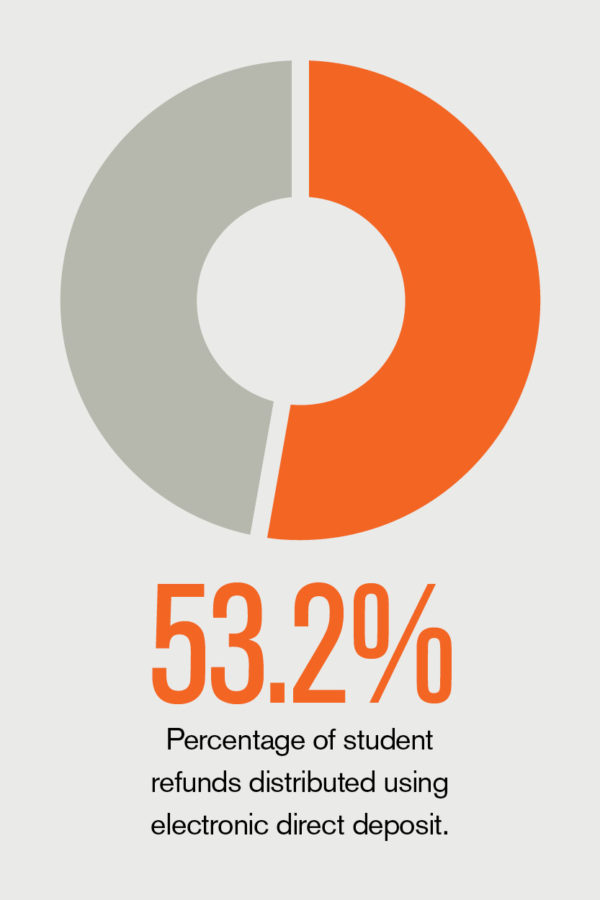
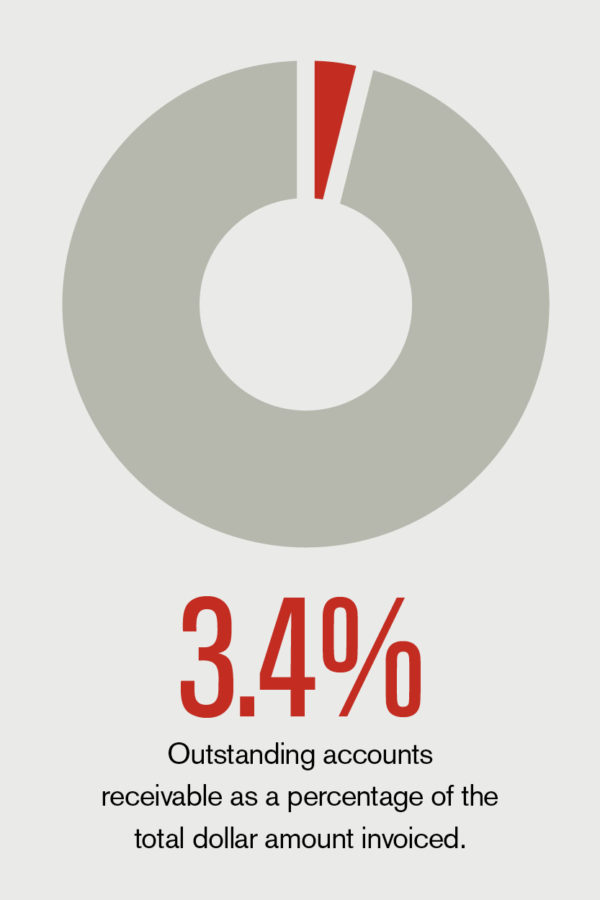
The first step in expeditiously handling any threat or incident is to have a tested plan in place. During their “Planning to Respond—Physical and Virtual Security” session at the NACUBO 2019 Annual Meeting, presenters Michael Kasitz, assistant vice president for public safety, and Judy Molnar, associate vice president for information technology and CIO, shared the steps Austin Peay State University, Clarksville, Tenn., has taken to build robust emergency management and cyber-incident response plans. For in-depth coverage of the annual meeting, read “Austin Inspired.”
Recent incidents of a gunman roaming the Austin Peay campus and of a phishing scam that compromised an employee’s direct deposit payment spurred leadership to strengthen action plans for safeguarding individuals, campus infrastructure, and the wider community.
Institutional response plans encompass a broad range of concerns—from business continuity to disaster recovery to cybersecurity. Ensuring that each plan remains fresh and relevant for those responsible for enacting it means providing up-to-date contact information and protocols about who needs to be notified. For instance, listed in Austin Peay’s cyber-response plan are the mobile phone numbers for IT, public relations, HR staff, legal counsel, and law enforcement to expedite the appropriate outreach.
The plan also includes external contact information, since the state of Tennessee requires that within 24 hours of any cybersecurity incident, its higher education institutions notify the state’s comptroller, secretary of state, and department of education, Molnar said.
Molnar and Kasitz offered additional advice for building effective response plans:
Envision the full range of potential threats. Beyond planning for the most likely natural disasters for your area—such as tornadoes, hurricanes, and flooding—identify the possible hazards hidden from view that may exist within the larger community. Are there industries in your region storing potentially lethal chemicals on-site?
Austin Peay’s annual review of its cyber response includes tabletopping a potential incident—playing out an incident as a means of assessing where to tighten business continuity protocols. Consider a scenario in which your institution’s finance system is brought down, and you can’t quickly bring it back online. How will that impact daily operations? Is there a workaround you can implement in the interim?
Scenario planning should also include incidents that could potentially damage the institution’s reputation and carry significant PR fallout, Kasitz said. Consider a situation where a high-level administrator is caught with pornography on his or her computer. Addressing this from a law enforcement standpoint may be unambiguous, but such an incident could potentially be disastrous for your institution’s brand if mishandled from a communications standpoint. Identify who is responsible for talking to the media and provide training so those individuals are comfortable speaking under stress in front of the cameras.
Train everyone. Trying toget all essential personnel to commit the time for training is difficult enough, but it may be nearly impossible to get everyone in the room at the same time. One solution is to run individual departments through an incident at separate times rather than trying to coordinate schedules for all departments. If full-day training proves too difficult, what can you do in two hours?
Training is essential not only for practicing a coordinated response, but also as a way to gather input and perspective. While IT staff best understand the technical nature of a cyberthreat, legal counsel, student services, HR, and other staff can provide important insights about how a situation may adversely impact the institution, students, or employees. At Austin Peay, cybersecurity student interns add another fresh perspective in helping the university assess specific components of cyberthreats.
Identify chain of response. In addition to leadership response, think about the range of support functions you need to include in your training—firefighting, environmental response, food services, utilities, and so forth. Develop an organizational chart of operations and support functions that could be impacted for any given incident. Likewise, consider that in an actual incident your president, provost, or other senior leaders may not even be on campus. Tabletopping with the full line of succession is important to ensure that you are training people in support roles to step in and take charge.
Don’t forget the details. Make clear to responders what should be documented in the moment so that you don’t forget what occurred in the heat of a crisis. For a cybersecurity response, the final report you may need to send to state officials and to your internal auditor should include a basic incident log of who you talked to, when, and about what.
In addition to a campuswide text-alert system, practice drills for securing-in-place until an all-clear signal is given. This helps ensure that everyone knows what to do when they are required to act in a crisis.
Finally, don’t forget about your larger community. Consider how you can direct volunteers who might show up to help in the event of a disaster. Where should they go, and what can you ask them to do?
KARLA HIGNITE, Fort Walton Beach, Fla., is a contributing editor for Business Officer.