In today’s world, innovations emerge at a stunning rate and are often sparked by technology advances or capabilities. Such is the case with electronic and digital signatures, which have made their way into the business world and hold potential to make higher education processes more efficient as well.
However, as with many new procedures, business officers must view the adoption of digital signatures against the canvas of overall risk and the level of authentication required for specific transactions.
At this point, there is still debate in many universities about whether to accept digital signatures, continue the status quo of “wet ink” signatures, or develop hybrid signature methods. Digital signature transaction-management platform solutions can streamline and automate document signing, validate signed documents within business processes, and securely archive all signed documents to help accelerate transactions and reduce costs.
The University System of Alaska Fairbanks has been researching and piloting the use of digital signatures in several areas, including the offices of bursars, admissions, procurement, and finance —with transactions ranging from internal approvals, tuition waivers, memos, and approvals on routine business communications. With our recent experiences in mind, we’ll share some advice on development and implementation of an effective digital signature process.
Definition and Differentiation
According to the Electronic Signatures in Global and National Commerce Act (ESIGN, 2000), an electronic signature is an electronic sound, symbol, or process attached to or logically associated with a record, and executed or adopted by a person with the intent to sign the record. A digital signature, on the other hand, refers to an encryption/decryption technology, on which an electronic signature solution is built.
A digital signature (a) achieves the collection of evidence of the document (via metadata, IP address, etc.), (b) verifies the identity of a signer/receiver, and (c) provides an audit trail of the transactions. Digital signatures are part of the process of electronic authentication that uses unique features called public or private key infrastructure. The private key is known only to the signer, while the public key is for anyone who receives the signed document. In the digital signature process, the document is encrypted with a private key by the signer and is decrypted by the receiver using a public key.
In layman’s terms, a digital signature, loosely referred to as an electronic signature, is a person’s electronic expression of his or her agreement to the terms of a particular document, with the intent to sign. Under the Uniform Electronics Transactions Act, the signatory is legally bound to the commitments made in the signed document. The electronic signature acts as an instrument of evidence regarding the authenticity of the electronic document in the same way as the handwritten signature does regarding paper-based documents.
Technical Details
While the technology requirements for creating the digital signature capability are fairly straightforward, it’s wise to conduct an infrastructure analysis and evaluation. The main areas to consider in the existing information technology environment include:
- Overall IT system evaluation and strategy. The system evaluation includes servers, network security, and application platforms. An important factor is the qualitative and quantitative estimation of the ways the systems’ current benefits align with institutional goals. The office of information technology coordinates the IT evaluation team, which includes representatives from various departments, and conducts the initial evaluation of the technology environment. Based on the results, strategic decisions are made regarding the areas suitable for pilot testing and implementation.
- Organizational structure. This assessment should include the nature of business processes in all functional areas, such as admissions, financial aid, human resources, facilities, athletics, and sponsored programs, that deal with financial transactions. There are areas where digital signature can be easily implemented, such as employee timesheets, timesheet approvals, human resource forms, employee benefits, and specific admissions and financial aid forms. However, the university policy needs to spell out clearly the business processes that can be conducted by digital signature approval methods.
- Security policy. The organizational security policy is mandated by various government regulations, such as FERPA, HIPAA, Sarbanes-Oxley, and others. The university’s risk management, legal counsel, internal audit, information security, and records information management departments are pivotal in providing key inputs to the policy.
Strategy and Implementation Steps
The institution’s culture change and process implementation can be just as important as the technical details.
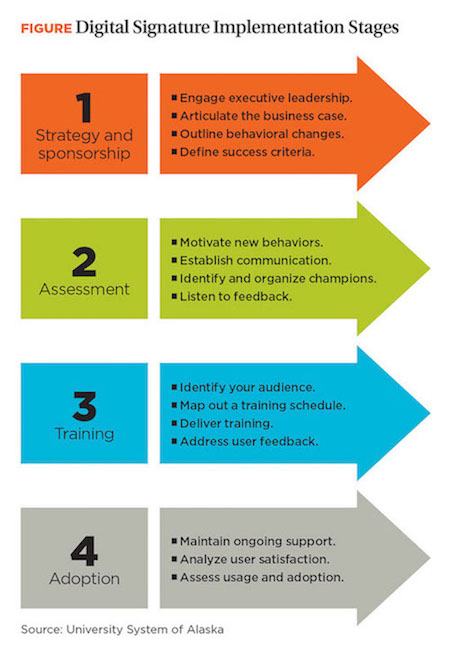
Before adopting a digital signature solution (or any technology solution), we considered four key steps (see figure above for details).
- Support and sponsorship. Securing executive support and stakeholder buy-in is critical to the evolution and implementation of the new process. In addition, electronic transactions connect a variety of functional areas; and, hence, a comprehensive change management plan and fully engaged executive sponsorship are critical to the success of the project. The initial phase of stakeholder buy-in involves the drafting of the digital signature policy, in collaboration with the university’s legal counsel, internal audit, information security, and records information management.
The draft can then be shared with the administrative heads of admissions, finance, budget, human resources, sponsored programs, and the registrar. The final draft policy, after approval by the legal, internal audit, and information security departments can then be adopted as university policy and published on the university website.
At the University of Alaska, our policy guidelines are in final draft stage, with various stakeholder groups currently reviewing them. Since we are closely aligned with the Tennessee Board of Regents, much of our policy reflects key points included in its signature policies.
- Assessment and feedback. In an effort to gauge support for the new signature process, it’s useful to develop a campuswide survey to assess the business need for digital signatures. The survey may include questions about the ways the digital signature aligns with the university’s goals, as well as legal and audit compliance.
A key factor to consider in implementing digital signatures is to identify the level of risk tolerance and the associated risk for a particular business process. University risks may involve financial, reputational, and other key administrative communications. Based on the various types of business processes and the level of severity, the assurance (which is a combination of authentication and validation) and trust levels have to be established. Functional area managers and organizations need to assess the level of risk, and to the extent to which one should secure the digital signature platform.
This correlation poses a trade-off challenge to business managers and organizations willing to accept digital signatures, thereby compelling them to identify those business processes that require optimum levels of authentication to offset risks.
- Digital signature rollout. Based on the functional area needs for digital signatures, a quick assessment of the number of transactions and the level of approval(s) required for a particular business process will provide a fairly accurate notion of the nature of the digital signature. For example, at most universities, the human resources benefits and health plan add/modify forms require a “wet ink” signature on any change to benefits or changes in health plans.
Each functional area determines the type of process (or forms) that may be substituted with digital signatures, sometimes setting a threshold on the monetary value for financial transactions below which all approvals may be authorized by digital signatures. One way to pilot the plan is to conduct a phased implementation in low-risk functional areas in which transactions are monitored for proper usage, unauthorized access, and security breaches.
With electronic transactions evolving at a rapid pace, digital signatures will become more acceptable. While the technology genie of digital signatures cannot be recaptured into the bottle, colleges and universities can balance the technology solution with the level of risk of acceptance to arrive at the best solution for their processes and practices.
SUBMITTED BY Shiva Hullavarad, enterprise content and electronic records administrator; Russell O’Hare, chief records officer; and Ashok Roy, vice president for finance and administration and CFO, at the University System of Alaska Fairbanks.